I had already told you how to access SQLite databases on Android in my previous article. Here in this article, we will have a look how we can exploit those databases to gather more sensitive informations.
I felt very interesting by playing around with SQLite databases in Android and it also gives me some knowledge about how android handles databases.
Among these databases, there are some highly sensitive information such like
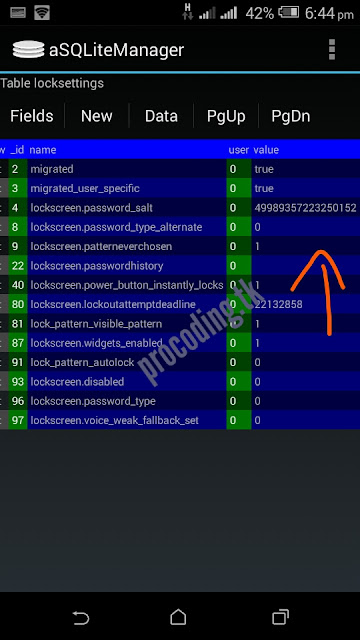
Lockscreen.db
Browser session ,
browser histories,
images loaded by the browser and more.
We can also penetrate into apps that are installed on our device to change its value and some legitimate informations too.
For example: I know some guys who where using apps like ‘GameGuardian’ to hack game scores.
We doesn’t need those apps to change game values if we have access to SQLite databases. But need Root Privilege.
We can just go into the databases and change things like how game Guardian does in games.
We can change every single information in that game more than any other game hacking application does.
Now let’s get into the matter.
Assuming you all read previous post.
Now,Go-to
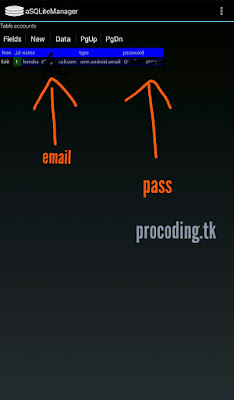
/data/system/users/0/accounts.db
Here we could notice the cryptographic versions of your E-Mail/G-Mail app password.
This is because I already told you every information of an application if stored by Android In it’s library.
But, the interesting part is, if you are navigating by using Android version 2.3
You can see the, the account password are stored in a plain text without properly encrypting it in cipher text.
[See the screenshot below]
But I couldn’t find this vulnerability in latest versions of Android.
This vulnerability becomes very dangerous if your device is rooted. If someone got physical access to your device ,he can just go to your root directory and he can pull out your passwords easily. Because of the reason that it is in plain text mode.
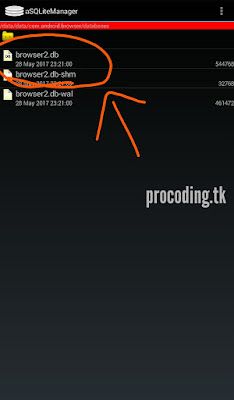
My next target is the internet browsers those are installed on our device.
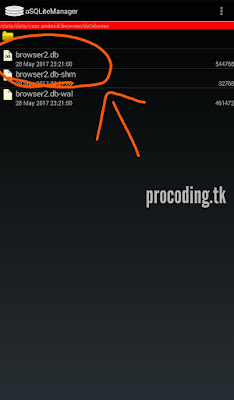
/data/data/com.exapmple.browser/databases/example.db
Here you could find all informations regarding your browser. This includes history ,bookmarks, images that you had loaded , images that you have downloaded, web searches, browser updates, saved passwords, web sessions , cookies and lot more.
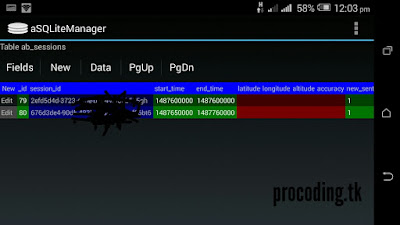
Here you can see an example of sessionID of a browser in my device.
But realistically we have no use with someone’s session sometimes . Because session ID is not always meant to be a permanent one . It keeps changing all the time when you logged out from your account. Also each time when you disconnect your Internet connection as well.
Yes but sometimes it does the job. If someone compromise your web browser and steal the session,also if you are still not logged out from your account, your session is still active in the server. There is a specific expire time for each sessionID. So the someone can easily use those session to make a login to your account.
Our method will be helpful for you if your friend’s device is rooted. If you got physical access to that device, you can grab those session ID for a making a successful login.
Notice:_)
I will not support these kind of malicious activities in someone’s account. This is really a punishable offence and the rest of your life would end up in jail. So be aware of the consequences!
Did you ever got thinking like, where are your Google profile photos and other photos that you had uploaded to your account stored in local device as cached?
Let’s take an example of Gmail apps in your Android device when you’re looking at your email account you can see your profile photo on on that Gmail app and this photo is stored on Google server.
The URL of your photo is stored on your Gmail app’s database folder. Which is not a really big deal. Because, every app does this thing in the same way itself.
That is what you can see in the below screenshot. Those are my email accounts. And straight to it, we can also see my profile photos URL. I just explained this thing just to make you understand how an app handles the file source.
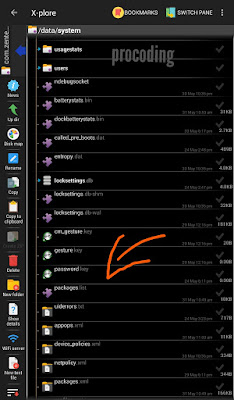
Let’s now talk about password.key file which is stored in
/data/system/password.key
This is a mixture of SHA-1 and Message Digest5 (md5) to ensure integrity.
Because of this ,the salted form of password. key can be found in password_salt.key.
Take a look at the following code to understand perfectly.
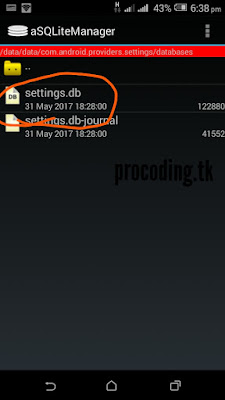
The password_salt.key is stored in
/data/system/com.android.Providers.Settings/databases/settings.db
Open settings.Db to find password_salt.Key
See below to understand how to provides integrity. 👇
-———-++———-+++——–+++– ———–++———-+++——–+++– ———–++———-+++——–+++–
public byte[] passwordToHash(String password) {** if (password == null) {**** return null;**** }**** String algo = null;**** byte[] hashed = null;**** try {**** byte[] saltedPassword = (password + getSalt()).getBytes();**** byte[] sha1 = MessageDigest.getInstance(algo = “SHA-1”).digest(saltedPassword);**** byte[] md5 = MessageDigest.getInstance(algo = “MD5”).digest(saltedPassword);**** hashed = (toHex(sha1) + toHex(md5)).getBytes();**** } catch (NoSuchAlgorithmException e) {**** Log.w(TAG, “Failed to encode string because of missing algorithm: " + algo);**** }**** return hashed;**
-———-++———-+++——–+++– ———–++———-+++——–+++– ———–++———-+++——–+++–
data/system/com.android.Providers.Settings/databases/settings.db ☝
Video Tutorial:- 👉 https://youtu.be/QQUX7brNECo
I am not explaining how you can crack those files. It’s not our subject here!
So let me conclude this article I hope you got how our Android handles databases.
There are still many portions to complete but I am concluding with this. You can learn in deep about Android databases from other sources.
Happy Hacking;-)